Authors: Paschal C. Amusuo, Kyle A. Robinson, Tanmay Singla, Huiyun Peng, Aravind Machiry, Santiago Torres-Arias, Laurent Simon, James C. Davis
Published on: October 21, 2023
Impact Score: 7.4
Arxiv code: Arxiv:2310.14117
Summary
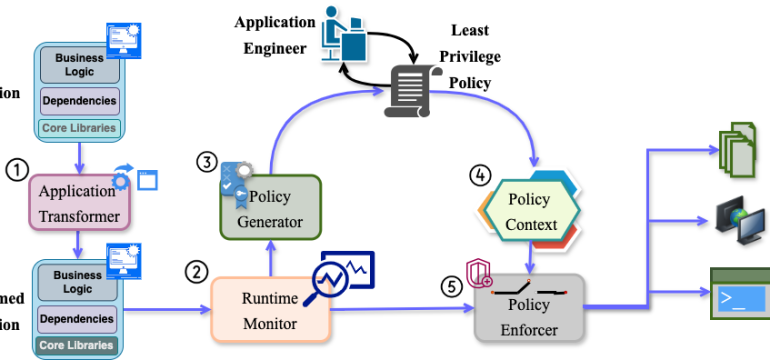
- What is new: Introduces Zero Trust Dependencies concept based on NIST Zero Trust Architecture for addressing security in third-party software components.
- Why this is important: Existing security defenses do not adequately protect against software supply chain attacks due to lack of comprehensive coverage on preventing malicious access, dependency awareness, and discovery of least privileges.
- What the research proposes: Proposal of Zero Trust Dependencies applying NIST Zero Trust Architecture principles specifically to software application dependencies, along with a system design (ZTDSYS) and a prototype for Java applications (ZTDJAVA).
- Results: ZTDJAVA successfully defends against common vulnerability classes in third-party software components with minimal overhead and ease of configuration and usage.
Technical Details
Technological frameworks used: NIST Zero Trust Architecture
Models used: Zero Trust Dependencies system design (ZTDSYS), Prototype (ZTDJAVA)
Data used: Study of third-party software components and vulnerabilities
Potential Impact
Cybersecurity solutions for software development and third-party component management, potentially impacting software development and security companies.
Want to implement this idea in a business?
We have generated a startup concept here: ZTrust Solutions.

Leave a Reply