Authors: Salko Korac, Leandros Maglaras, Naghmeh Moradpoor, Bill Buchanan, Berk Canberk
Published on: March 26, 2024
Impact Score: 7.4
Arxiv code: Arxiv:2403.17571
Summary
- What is new: The shift in cybercriminal strategies from using RSA and AES encryption to a variety of other methods in Linux ransomware, highlighting its early development stage and potential growth similar to Windows-based malware.
- Why this is important: Linux systems are increasingly targeted by ransomware, posing a threat to IoT ecosystems. Existing forensic techniques need evaluation for their applicability and effectiveness against these emerging threats.
- What the research proposes: Investigation of current forensic methods applied to Linux ransomware to evaluate their maturity and impact, identifying the need for new strategies due to the evolving encryption methods used by cybercriminals.
- Results: Identified a shift in encryption strategies among Linux ransomware creators, implying a gap in current forensic methods and the need for adaptation. Presented evidence that Linux ransomware is at an early stage, with significant potential for damage.
Technical Details
Technological frameworks used: nan
Models used: RSA, AES, Variety of other encryption techniques identified in Linux ransomware
Data used: nan
Potential Impact
IoT industry, including providers of cloud infrastructure, IoT gateways, and security solutions, may need to re-evaluate their security and forensic approaches.
Want to implement this idea in a business?
We have generated a startup concept here: ShieldX IoT Security.
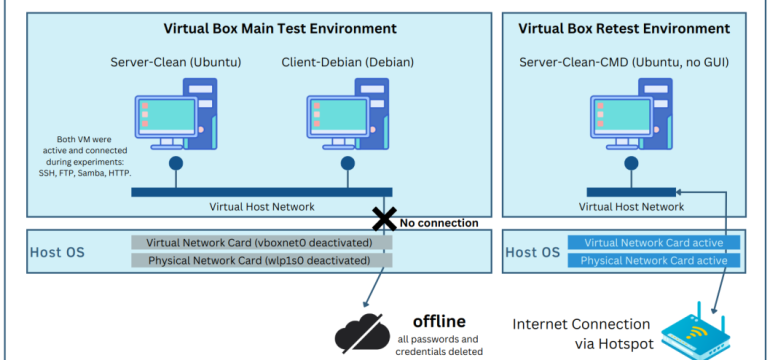

Leave a Reply